Digital Forensics - Chuck Eastsom - Lab 4
Lab Access for Digital Forensics, Investigation, and Response, Fourth Edition
Part 1: Analyze PCAP for Forensics Evidence
Plot: The lab involves incident response scenario where confidential files were exfiltrated from the corporate network. We are conducting forensic investigations using NetWitness Investigator Freeware and Paraben’s E3.
Network Traffic Analysis
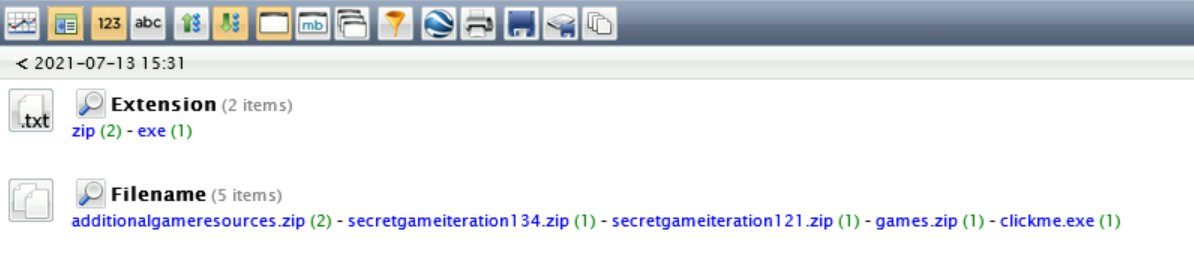
The security incident involved exfiltration of confidential company data - we are analyzing pcap and found the files below that were exfiltrated by the user.
NetWitness Investigator is an enterprise-level threat analysis platform developed by RSA and designed to contextualize network activity and efficiently identify malicious activity
Part 2: Analyze Disk Image for Forensic Evidence
-
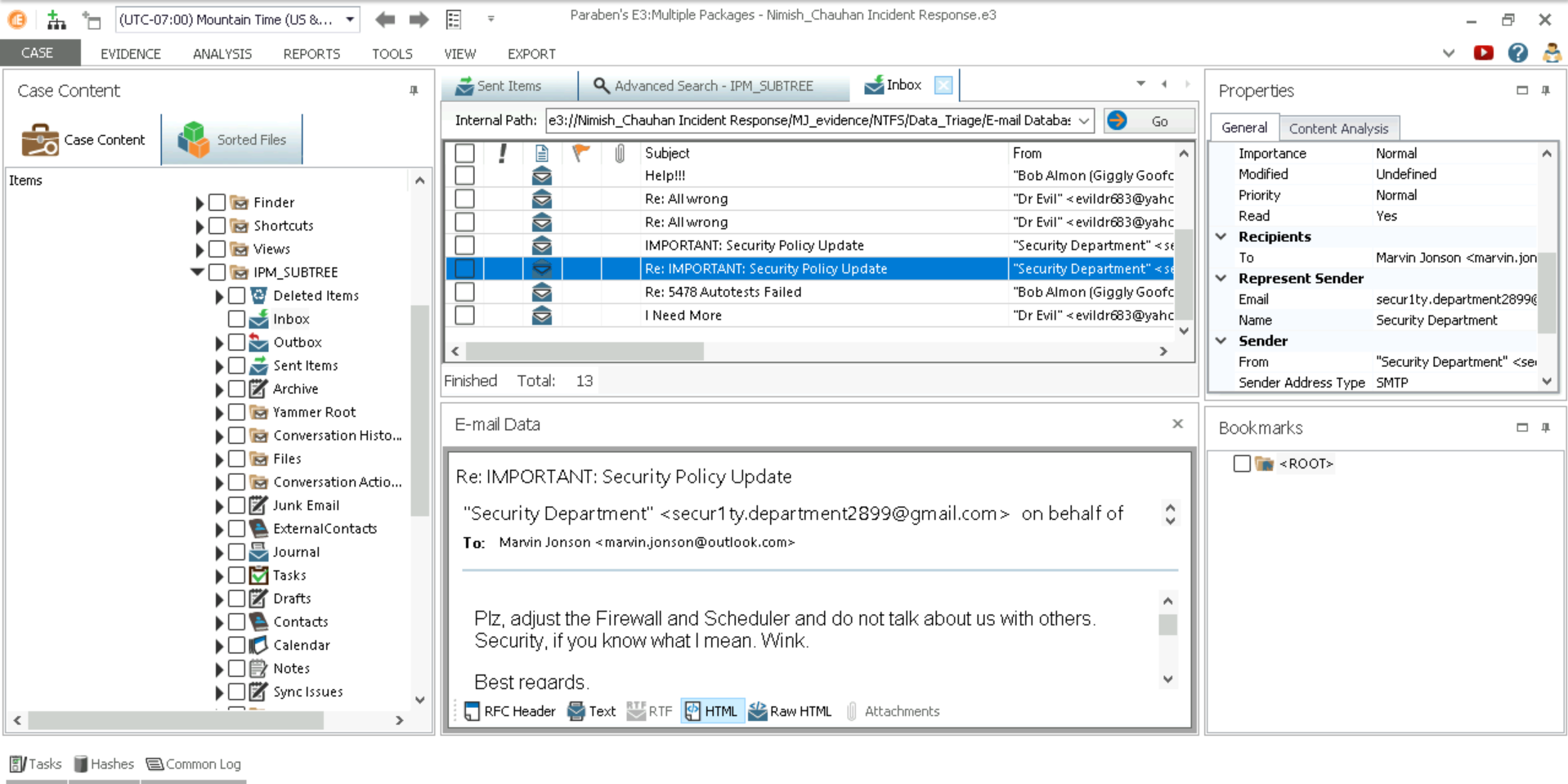
Email Forensics - The disk image was taken from the laptop of a Giggly Goofo employee named Marvin Jonson, whom the security team have reason to suspect may be involved in the data exfiltration incident. We will use E3 to analyze and look through content.
We found emails from Marvin’s disk image during forensics that clearly depicts malicious instructions provided by the threat actor. Below is the evidence.
Instructions to change firewall rules
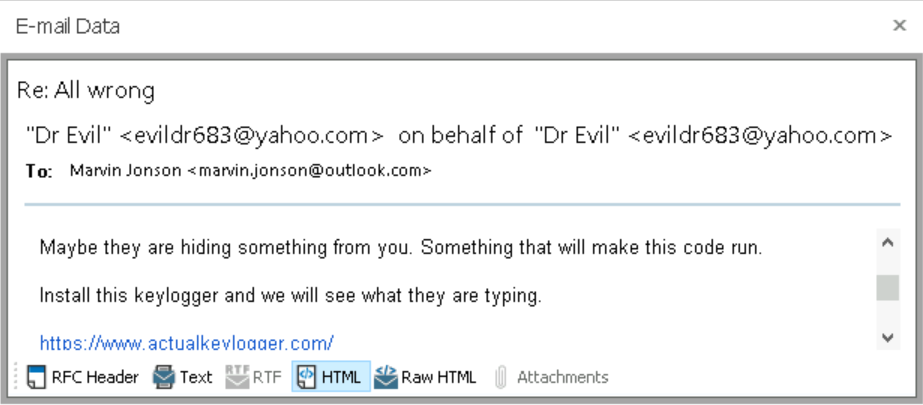
Asking to install keylogger, which can record all key activities
-
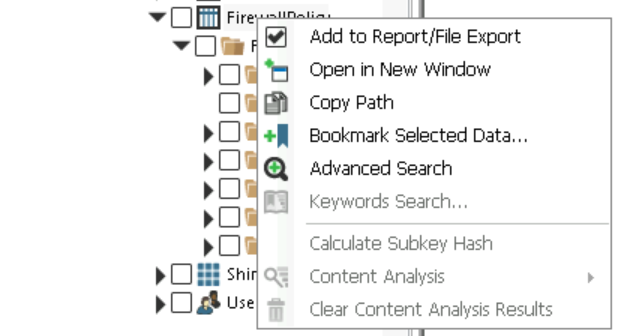
Registry forensics - Checking firewall rules and installation location of keylogger
- Advanced Search in Firewall Policy under - Incident Response -> Registry -> Data Triage
-
Open Result and analyze data for keylogger -
Port - 666
Location - C:\ProgramData\SecurityMonitor\{AKC34567-KCQR-WW34-AK47-INUM489023MY}\akl.exe
Name - Actual Keylogger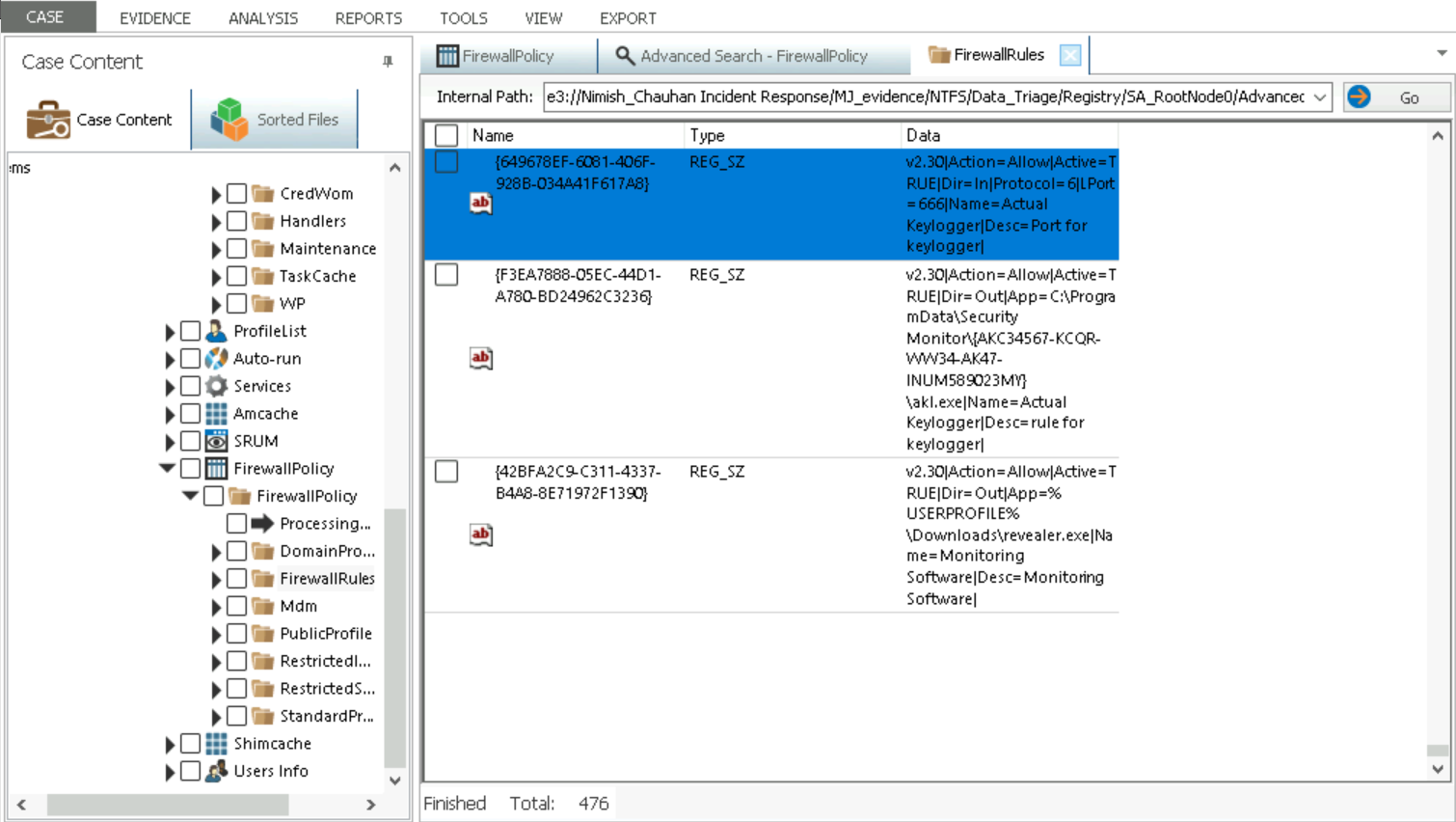
- Advanced Search in Firewall Policy under - Incident Response -> Registry -> Data Triage
Attack Timing -
`Start Time - 1625087483 - Wednesday, June 30, 2021 9:11:23 PM
`End Time 0
`Expiration Time - 1627679483 - Friday, July 30, 2021 9:11:23 PM
`Last Modified Time - 1625087483
These Labs are based on Digital Forensics, Investigation, and Response 4th Edition by Dr Chuck Easttom