Digital Forensics - Chuck Eastsom - Lab 2
Lab Access for Digital Forensics, Investigation, and Response, Fourth Edition
Section 1: Hands on Demonstration
Part 1 Detect Steganography Software on a Drive Image
- We will be checking if stegnography software has been installed on user’s/suspect’s drive image using a specialized hash database.
- Specialized Hash Database - Contains MD5 hash values of popular steganography tools. It can help detect software even if name has been changed to hide software itself.
-
Open E3
-
Open Case
-
Add Evidence File (Existing in this case) & Import Hash Database for comparing image hashes with hash database to check if the user has installed any stegnography applications to hide content.
-
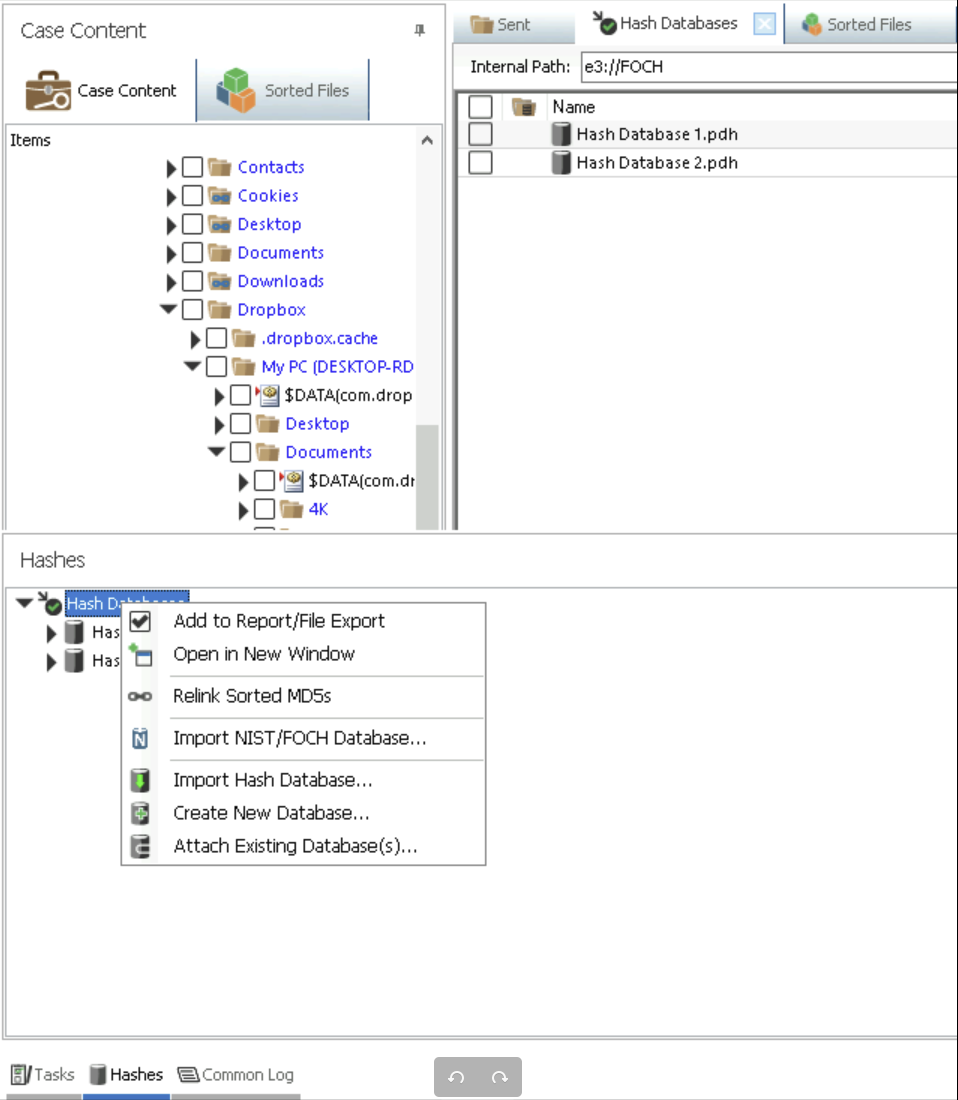
Import Hash Database 1.pdh from bottom left corner Hashes option. In this virtual machine, hashes were pre downloaded, you can download similar databases from NIST
-
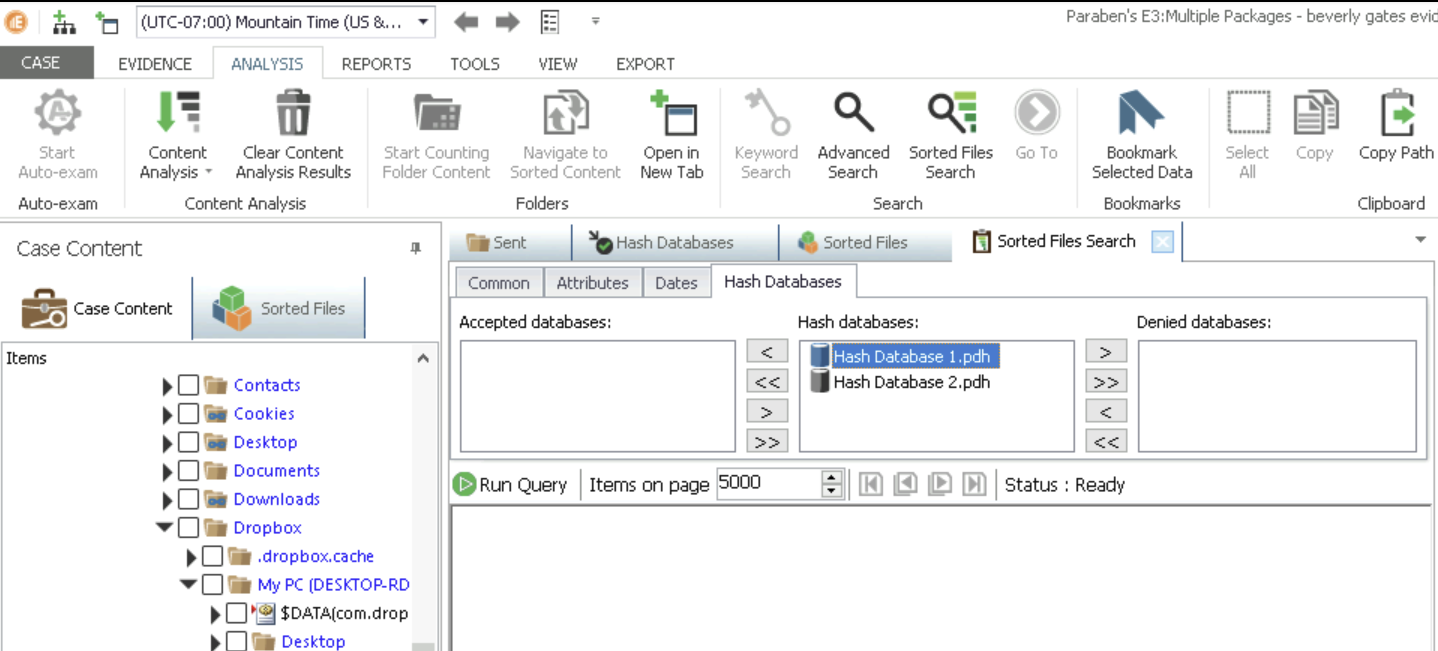
Then Go to Analysis -> Sorted Files Search 1
-
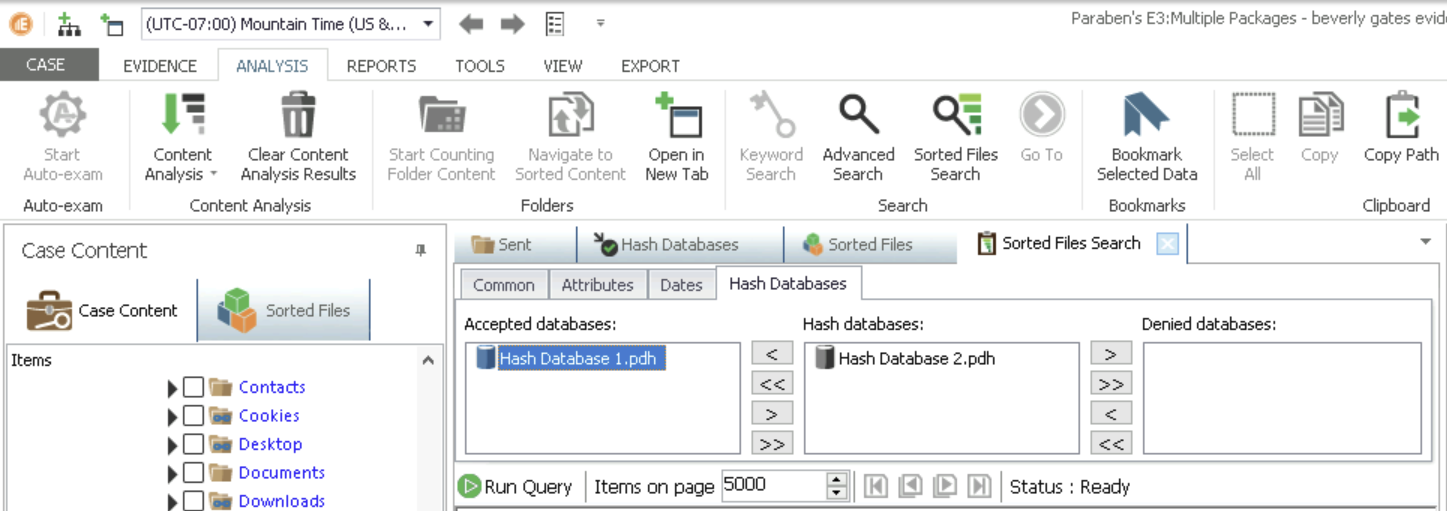
Move Hash Database 1.pdh to Accepted databases
-
Now Check Sorted Files(on left) -> Run Query
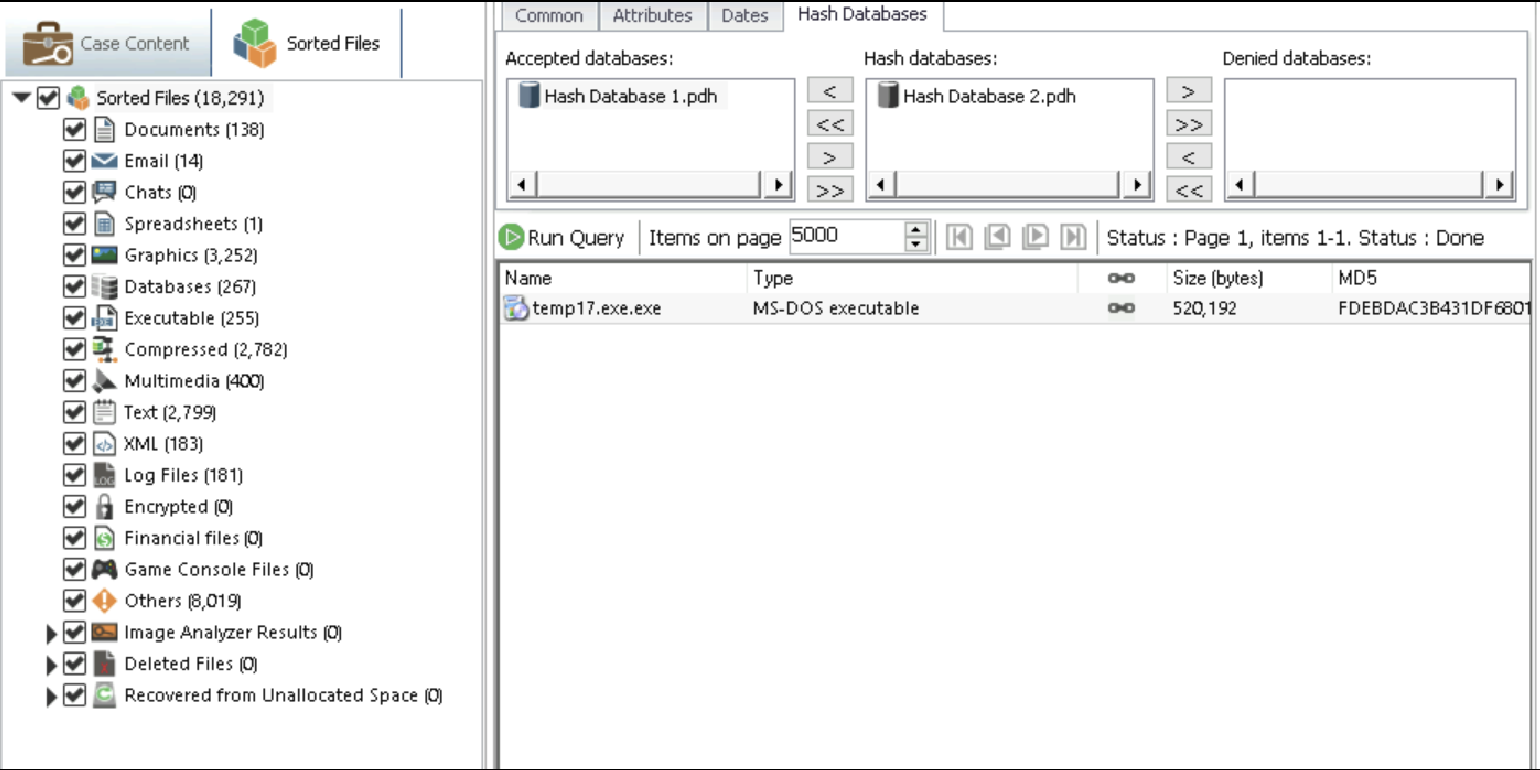
-
Found One Entry -> Open using Show Links
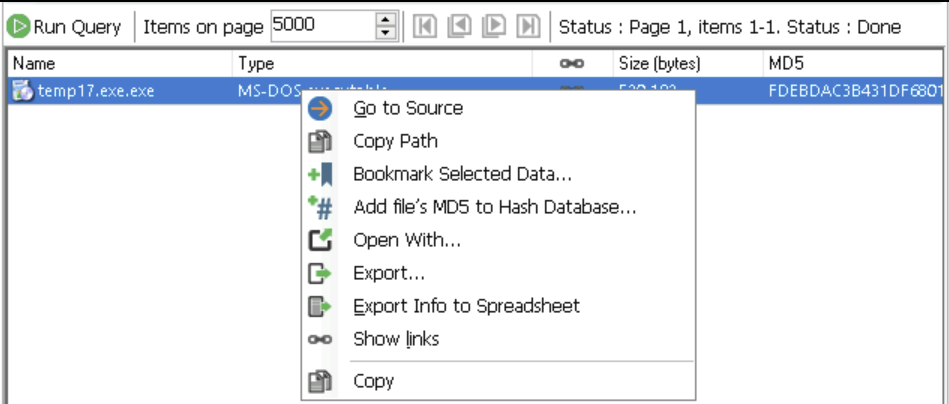
-
Turns out this is renamed file of OpenPuff tool which means some data might be hidden by suspect here using this OpenPuff
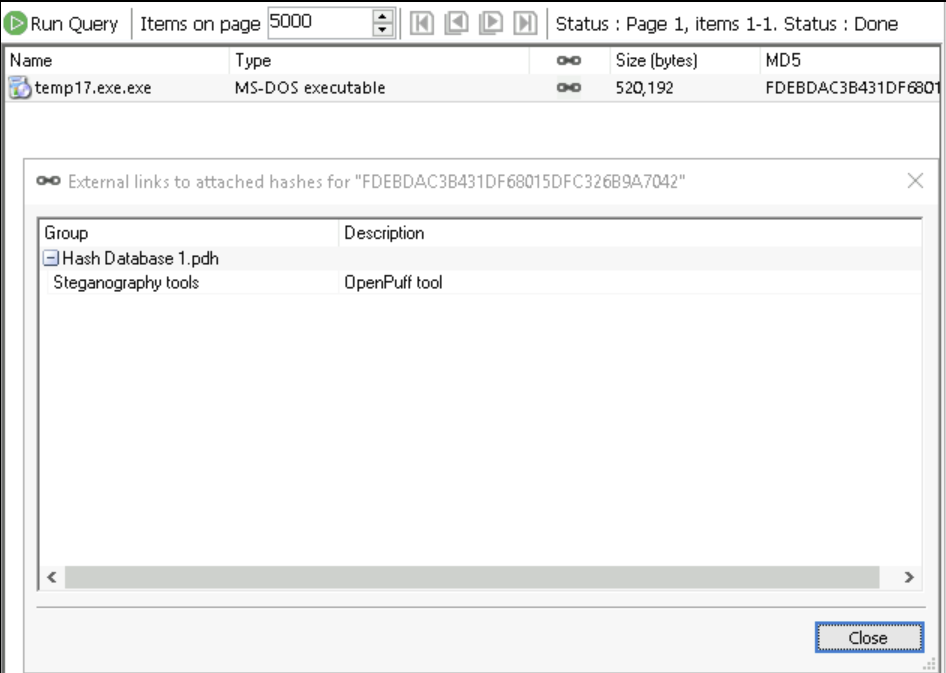
-
Part 2: Detect Hidden Data in Image Files
-
Lets say we found a suspicious folder with multiple files - GIFs, txt, etc.
-
First Export Folder to another location by Right Click -> Export
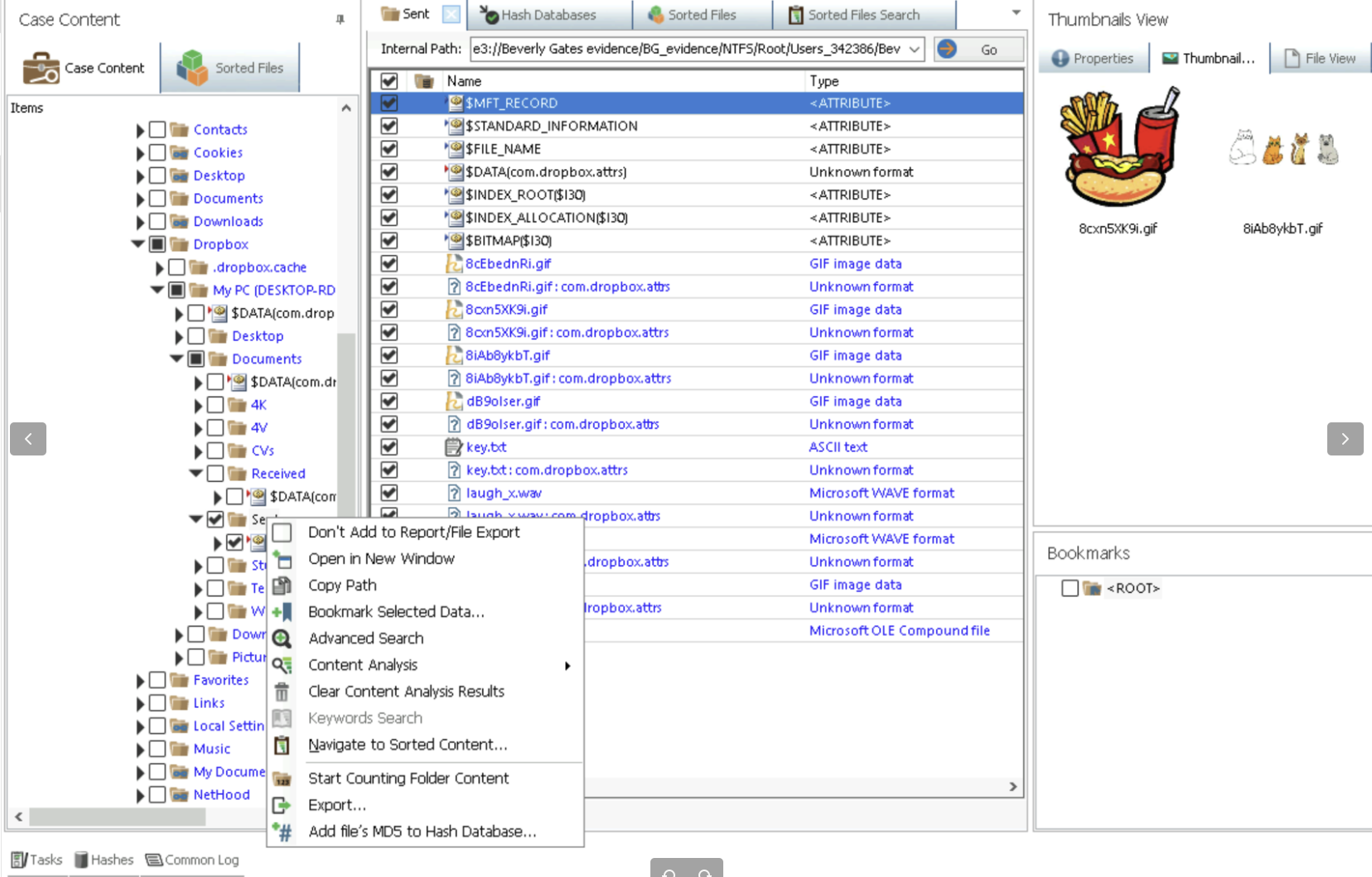
-
Use StegExpose to find which file has hidden data
java -jar "C:\Program Files (x86)\StegExpose-master\StegExpose.jar" "C:\Users\Administrator\Documents\E3 Cases\Beverly Gates evidence\Sent"- Location of StegExpose:
C:\Program Files (x86)\StegExpose-master\StegExpose.jar - Location of Folder:
C:\Users\Administrator\Documents\E3 Cases\Beverly Gates evidence\Sent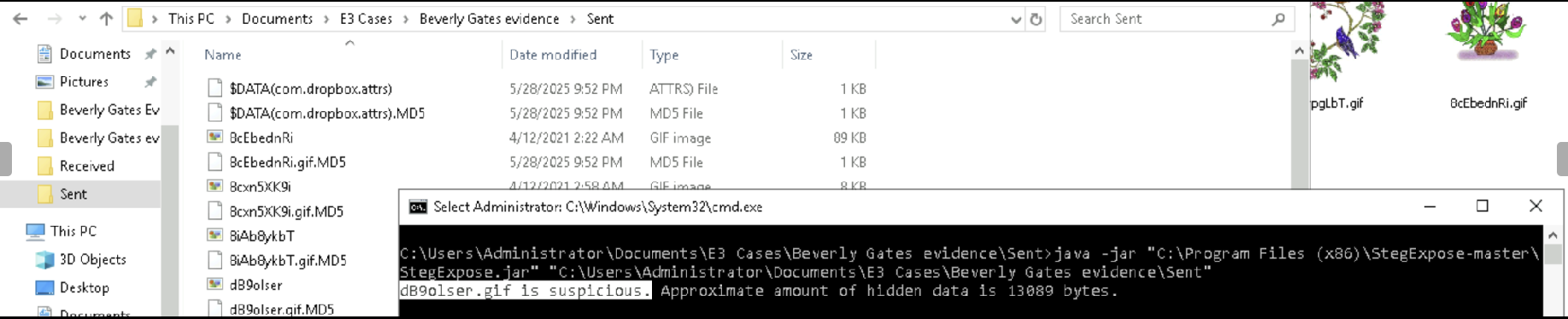
- Location of StegExpose:
These Labs are based on Digital Forensics, Investigation, and Response 4th Edition by Dr Chuck Easttom